Creating a mind map for vulnerability management is a structured, collaborative approach to vulnerability remediation. By visually organizing threats, risks, remediation steps, and responsibilities, vulnerability management mind maps help security teams streamline workflows, improve clarity, and enhance collaboration.
In this guide, we'll explore cases showing how to use mind maps for vulnerability management to make your security operations more efficient and actionable. By reading this article, you'll also be able to create a vulnerability management mind map with AI, so let's get started!
What is vulnerability management?
The vulnerability is a security risk in digital system, and the vulnerability management is like a long-term plan of full physical examination and health maintenance for digital systems. It continuously monitors and discovers vulnerabilities in the system, assesses the degree of harm of these vulnerabilities, and then quickly repairs or takes temporary protective measures. The ultimate goal is to reduce the risk of system attacks and protect corporate data, user privacy and normal business operations.
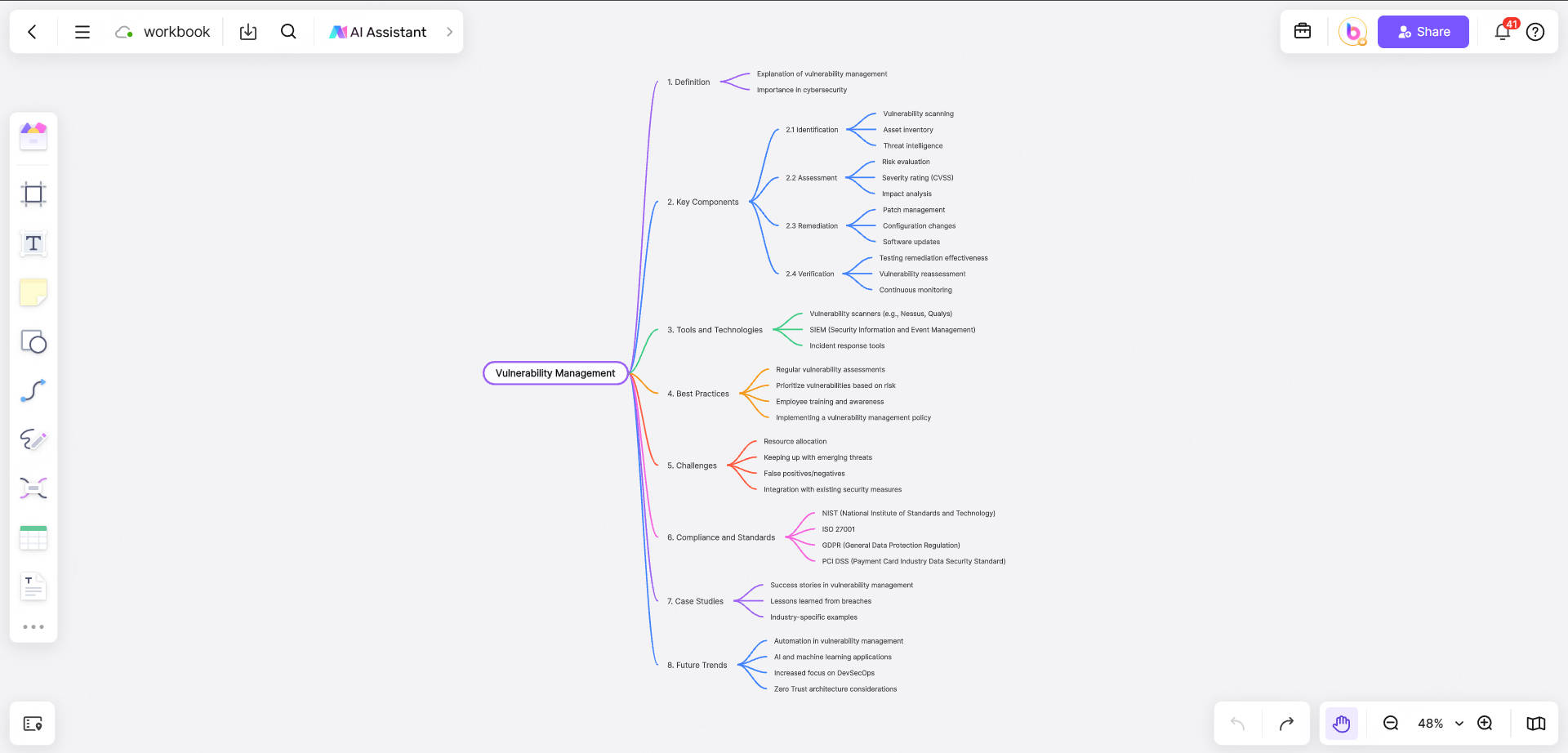
There are the core actions of vulnerability management:
Regular inspection: Use tools to scan servers and applications, like using an X-ray machine to find "hidden dangers".
Risk classification: Not all vulnerabilities are fatal, and it is necessary to determine which ones need to be dealt with immediately (such as those that can directly lead to data leakage) and which ones can be postponed.
Repair and protection: "Patch" the vulnerabilities or add protection rules, such as updating the software version and closing high-risk ports.
Keep an eye on: After the repair, it is necessary to review whether it is successful and monitor whether new vulnerabilities appear.
Basic Vulnerability Management Mind Map
The basic vulnerability management mind map is a visual navigation map with the "vulnerability management life cycle" as the core. It is designed for small and medium-sized enterprises or teams that are new to vulnerability management. It aims to simplify the complex vulnerability management process into an intuitive operation guide.
It starts with asset inventory, guiding users to systematically sort out key assets such as servers, applications, network equipment, and clarify the protection objects. Then vulnerability scanning, risk assessment, repair strategy, verification and monitoring are carried out in sequence, which forms a complete vulnerability management closed loop.
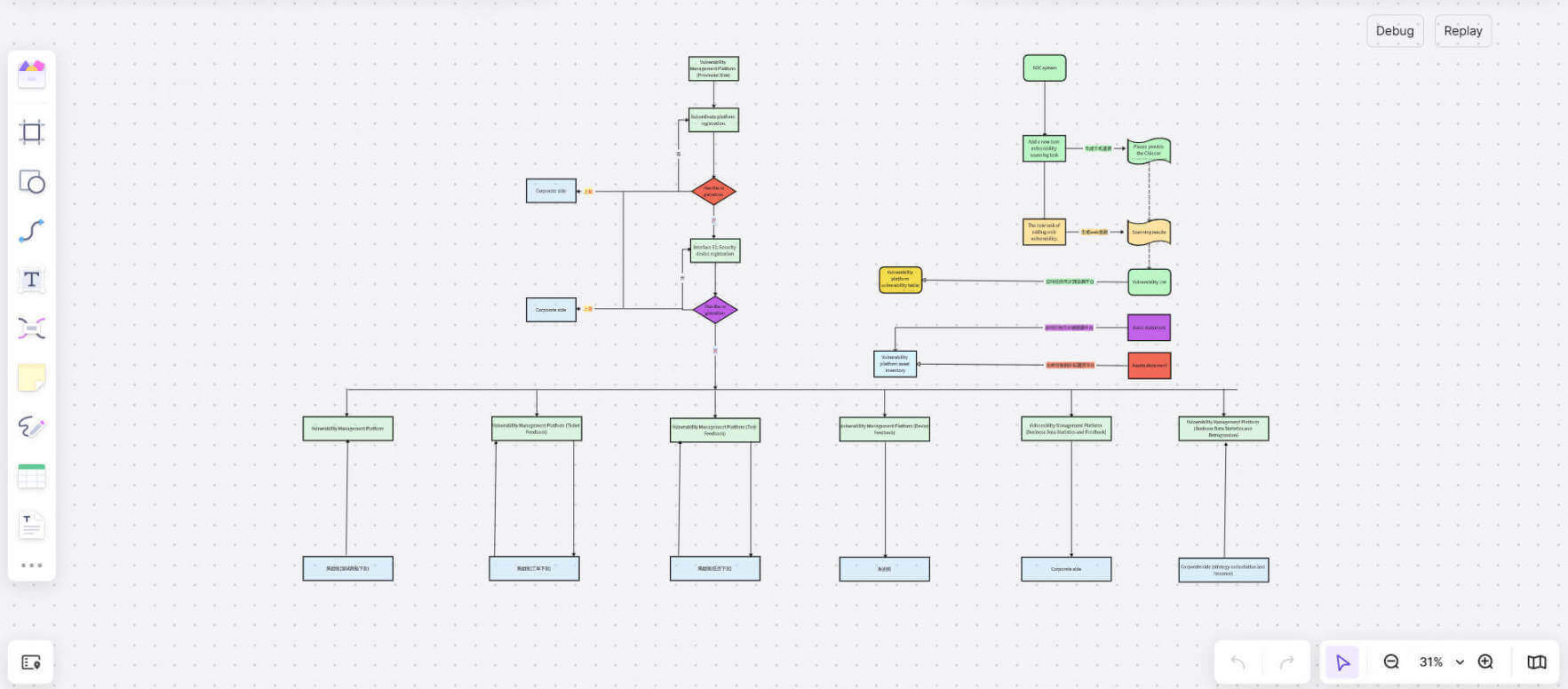
This vulnerability management map is suitable for small and medium-sized enterprises with limited resources but need to quickly build a basic protection system. It can not only prevent the team from getting lost in the complex process, but also greatly reduce the operation threshold through color marking, layered logic and key node reminders. It is a practical tool for vulnerability management from chaos to order.
Risk-Based Prioritization Mind Map for Vulnerability Management
The risk-based prioritization mind map is a decision-making framework that focuses on priorities.
The map is centered on the vulnerability priority matrix. First, it integrates multi-source inputs - from automated scanning reports to external threat intelligence to user feedback to ensure that vulnerability information is not missed; then it dynamically assesses risks by using the two key dimensions of possibility and business impact.
In terms of design, icons such as 🔥(urgent), ⚠️ (warning), and ⏳ (delayable) are used instead of plain text annotations, so that even non-technical personnel can identify priorities at a glance.
This map is particularly suitable for enterprises with complex attack surfaces that need to balance efficiency and resources, helping teams to accurately identify targets that must be dealt with immediately from vulnerabilities.
Mind Map for Vulnerability Management in Team Collaboration
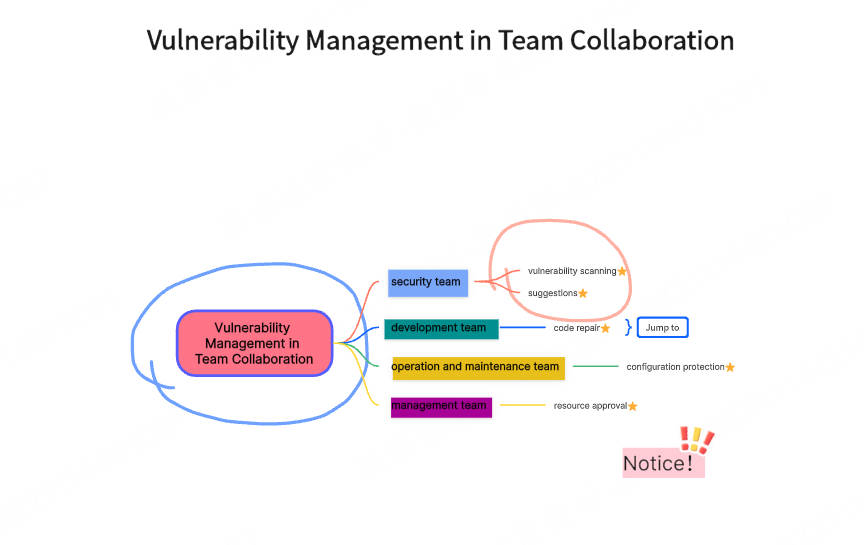
This mindmap for vulnerability management in team collaboration is like "collaborative combat map" that breaks down departmental barriers. It is designed for large enterprises or cross-functional teams to solve the common communication gaps and unclear responsibilities in vulnerability repair.
This vulnerability management mind map starts with the division of roles, clarifies the responsibility boundaries of the security team (vulnerability scanning and suggestions), development team (code repair), operation and maintenance team (configuration protection), and management (resource approval), and connects the actions of various departments through collaborative processes.
In terms of design, blue, green, and yellow colors distinguish departmental responsibilities, combined with hyperlinks to jump to internal documents, greatly reducing the cost of cross-team collaboration.
Tips for Designing Mindmap for Vulnerability Management
✔Strengthen visual contrast: On the basis of color marking (red/orange/green), superimpose icon symbols - for example, use 🔥 to represent high-risk vulnerabilities, ⚠️ to represent unrepaired items, and 🛡️ to represent protected assets. Even when printing in black and white, you can quickly identify priorities through symbols.
✔Layered folding logic: Use the **"fold/expand" function** of the mind map to display only the first-level branch by default, such as "asset list" and "vulnerability scan". After clicking, you can view tool command examples, lists of responsible persons and other details layer by layer to avoid information overload.
✔Dynamic timeline marking: Insert the **"last updated time" label** next to the scan frequency and repair deadline nodes, such as "Last scan: 2025/03/05".
✔Related document jump: Use online mind maps such as Boardmix to embed hyperlinks in the "repair strategy" branch to directly jump to the internal vulnerability repair SOP document or patch download page to reduce cross-platform search costs.
✔Reserve a blank comment area: Add a "Notes" subnode at the end of each branch to encourage the team to record temporary adjustment plans (such as "due to system compatibility delays, use firewall interception instead") to retain traces of flexible responses.
Creating Mind Map for Vulnerability Management with Boardmix
Managing vulnerabilities is no easy task. From tracking security flaws to coordinating remediation efforts across teams, the process can quickly become overwhelming. But what if you could simplify it with AI-powered visual collaboration?
With Boardmix, security teams can transform complex vulnerability management workflows into structured, easy-to-follow visual maps—improving efficiency, clarity, and cross-team collaboration. Let’s explore how.
Skip the Manual Work, Generate a Vulnerability Management Framework in Minutes
One of the biggest challenges in vulnerability management? Starting from scratch.
Creating a structured vulnerability management framework typically requires manual effort, research, and alignment across teams. But with Boardmix, you can bypass the tedious setup and let AI do the heavy lifting.
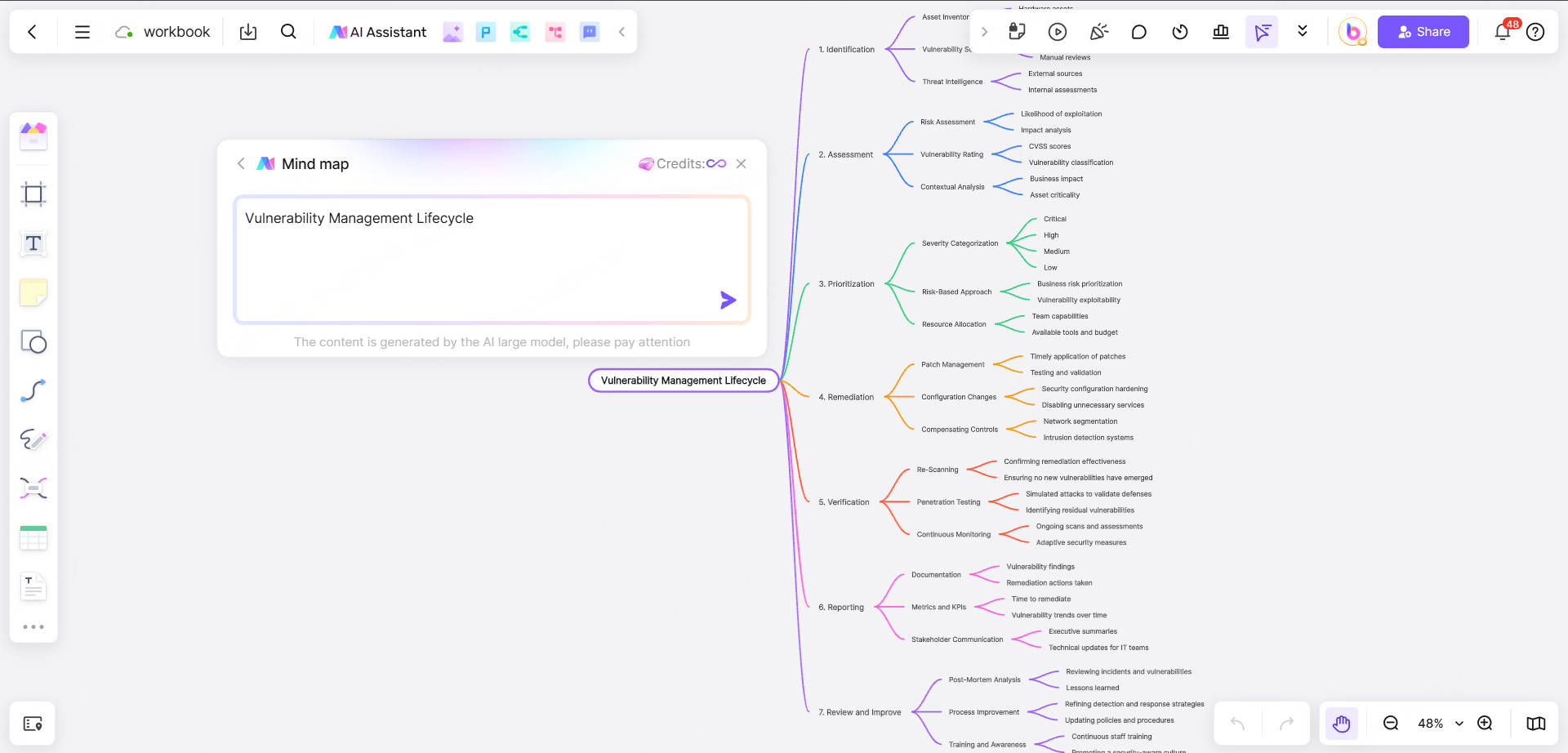
Just enter the keyword “Vulnerability Management Lifecycle,” and Boardmix AI instantly generates a standardized mind map.
Customize with ease: security teams can modify the AI-generated diagram to include compliance requirements, department responsibilities, or custom workflows. What used to take hours now takes just 5 minutes!
No More Scattered Information, Bring Everything into One Place
A common frustration in security workflows? Critical information is everywhere. Vulnerability reports, patch instructions, and test results often live across multiple platforms—making it hard to track progress or access key details when needed.
With Boardmix, you can centralize everything in one visual space:
Attach key documents directly to diagram nodes: embed PDF vulnerability reports, Excel patch details, or even video walkthroughs of penetration tests.
Use visual status markers like 🚨 (High Risk), ✅ (Fixed), or ⏳ (Pending Review) to track progress at a glance.
Different Roles, Different Needs, One Tool for Everyone
Security operations involve multiple stakeholders, each requiring different levels of detail. Executives want big-picture insights, while security analysts need step-by-step breakdowns.
With Boardmix, you can switch between views to suit each role’s needs:
Convert diagrams into sortable tables: sort vulnerabilities by CVSS score, remediation deadlines, or resource allocation priorities.
Collapse non-relevant branches: so IT teams can focus only on the server vulnerability fixes they’re responsible for.
Break Down Communication Barriers and Enable Real-Time Cross-Team Collaboration
Security teams don’t work in isolation, and effective vulnerability management requires coordination with IT, development, and compliance teams.
Yet, miscommunication is a major issue: emails get buried, spreadsheets go out of sync, and tasks slip through the cracks.
Boardmix makes it easy to stay aligned:
Real-time collaboration: Security, IT, and DevOps teams can update diagrams simultaneously, marking progress as they go (e.g., DevOps tags “Patch Deployed,” IT marks “Firewall Updated”).
Full revision history: Need to trace back decisions? Boardmix records every change for easy auditing.
While handling the Heartbleed vulnerability, security, IT, and development teams use @mentions in comments to synchronize updates—cutting remediation time from 3 days to just 8 hours.
Ready to transform your vulnerability management process? Try Boardmix for free today and experience the power of AI-driven security workflows. Visit Boardmix now and create your first vulnerability management map, because smarter security starts with better collaboration.